Failed to Connect to Firepower Continuing Without It
This document describes the Smart License registration configuration of Firepower Management Center on Firepower Threat Defense-managed devices.
Requirements
There are no specific requirements for this document.
Components Used
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
FMC, FTD, and Smart License registration.
Smart License registration is performed on the Firepower Management Center (FMC). The FMC communicates with the Cisco Smart Software Manager (CSSM) portal over the internet. In the CSSM, the firewall administrator manages the Smart Account and its licenses. The FMC can freely assign and delete licenses to the managed Firepower Threat Defense (FTD) devices. In other words, the FMC centrally manages licenses for FTD devices.
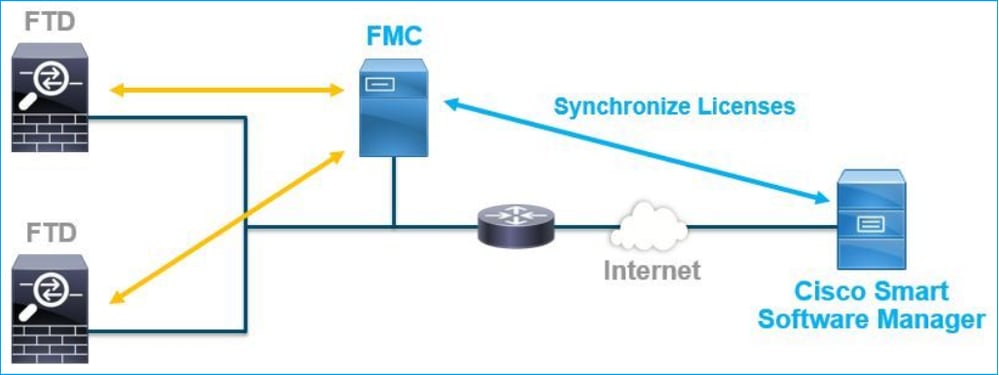
An additional license is required to use certain features of FTD devices. The Smart License types customers can assign to an FTD device are documented in FTD License Types and Restrictions.
The Base license is included in the FTD device. This license is automatically registered in your Smart Account when the FMC is registered to CSSM.
The term-based licenses: Threat, Malware, and URL Filtering are optional. To use features related to a license, a license needs to be assigned to the FTD device.
To use a Firepower Management Center Virtual (FMCv) for the FTD management, a Firepower MCv Device License in CSSM is also needed for the FMCv.
The FMCv license is included in the software, and it is perpetual.
Additionally, scenarios are provided in this document to help troubleshoot common license registration errors that can occur.
For more details about licenses check Cisco Firepower System Feature Licenses and Frequently Asked Questions (FAQ) about Firepower Licensing.
Prerequisites
1. For Smart License registration, the FMC must access the internet. Because the certificate is exchanged between the FMC and the Smart License Cloud with HTTPS, ensure there is no device in the path that can affect/modify the communication. (for example, Firewall, Proxy, SSL Decryption device, and so on).
2. Access the CSSM and issue a Token ID from Inventory > General > New Token button, as shown in this image.
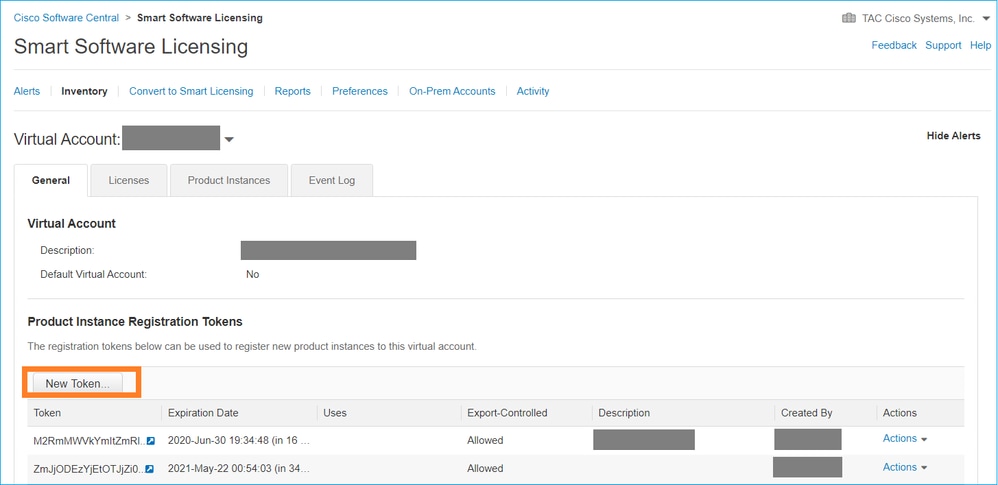
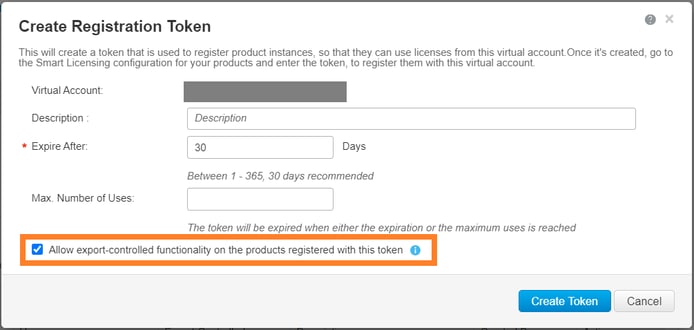
To use strong encryption, enable the Allow export-controlled functionality on the products registered with this token option. When enabled, a checkmark displays in the check box.
3. Select Create Token.
FMC Smart License Registration
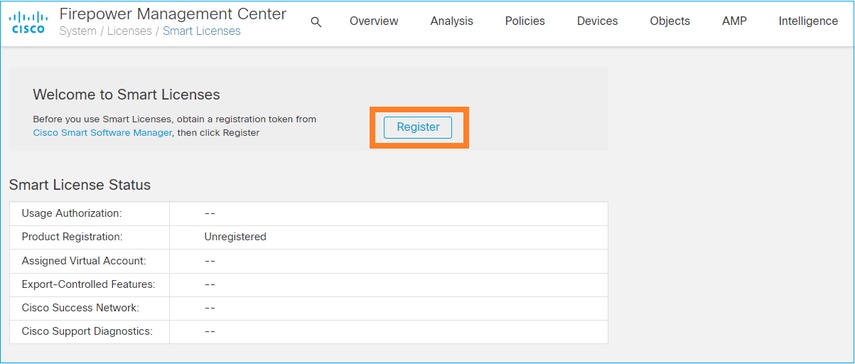
Navigate to the System> Licenses > Smart Licenses on the FMC, and select the Register button, as shown in this image.
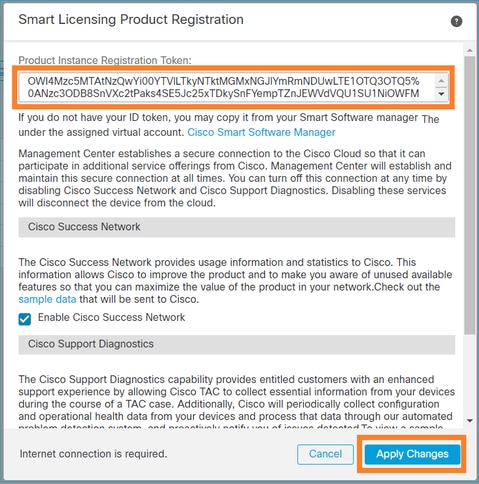
Enter the Token ID in the Smart Licensing Product Registration window and select Apply Changes, as shown in this image.
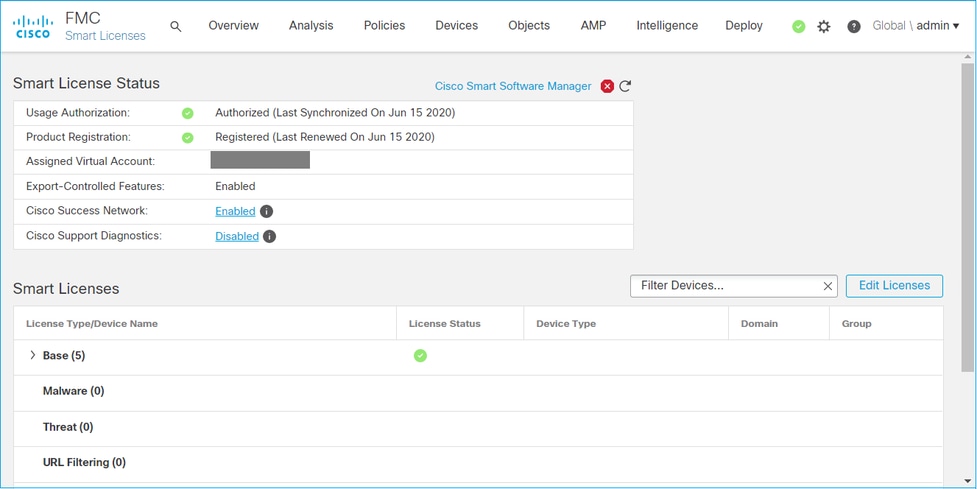
If the Smart License registration was successful, the Product Registration status shows Registered, as shown in this image.
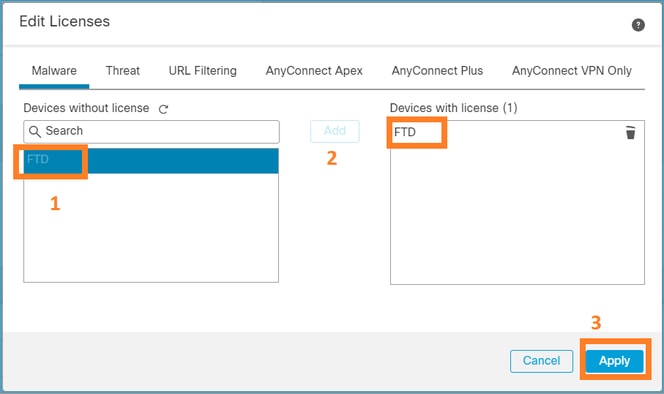
To assign a term-based license to the FTD device, select Edit Licenses. Then select and add a managed device to the Devices with license section. Finally, select the Apply button as shown in this image.
Confirmation in Smart Software Manager (SSM) Side
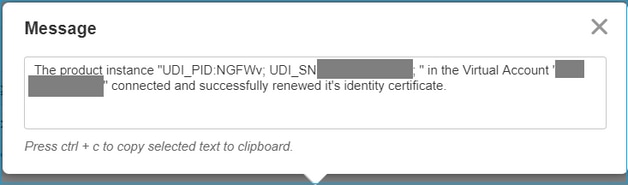
The success of the FMC Smart License registration can be confirmed from Inventory > Event Log in CSSM, as shown in this image.
The registration status of the FMC can be confirmed from Inventory > Product Instances. Check the event log from the Event Log tab. Smart License registration and use status can be checked from the Inventory > Licenses tab. Verify the term-based license purchased is used correctly and there are no Alerts that indicate insufficient licenses.
FMC Smart License De-Registration
De-register the FMC from the Cisco SSM
To release the license for some reason or use a different token, navigate to System > Licenses > Smart Licenses and select the de-register button, as shown in this image.
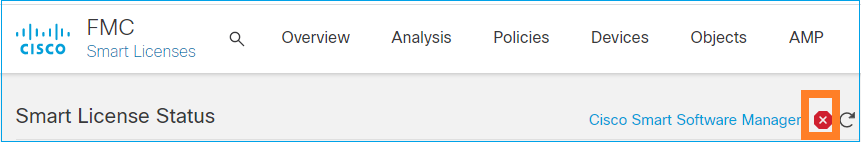
Remove Registration from SSM Side
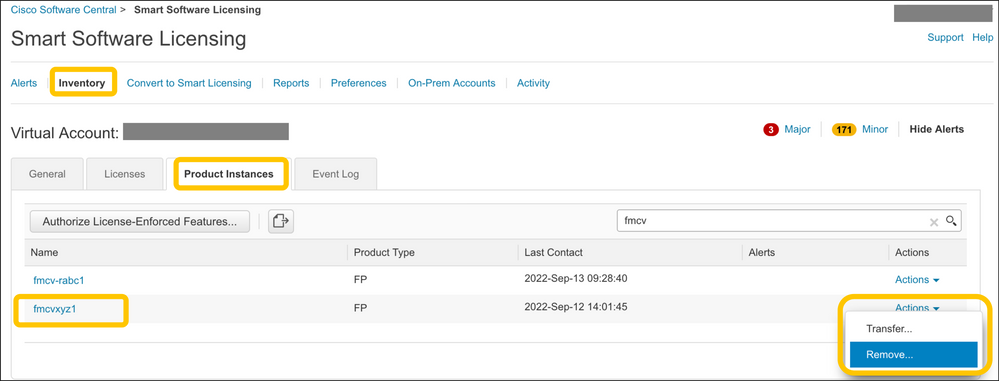
From the Inventory > Product Instances, select Remove on the target FMC. Then select Remove Product Instance to remove the FMC and release the allocated licenses, as shown in this image.
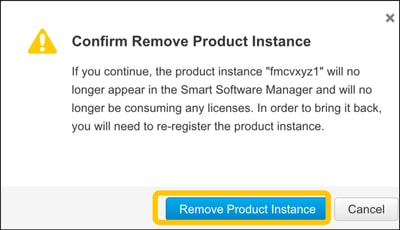
Time Synchronization Verification
Access the FMC CLI (for example, SSH) and ensure the time is correct and it is synchronized with a trusted NTP server. Because the certificate is used for Smart License authentication, it is important that the FMC has the correct time information:
admin@FMC:~$ date Thu Jun 14 09:18:47 UTC 2020 admin@FMC:~$ admin@FMC:~$ ntpq -pn remote refid st t when poll reach delay offset jitter ============================================================================== *10.0.0.2 171.68.xx.xx 2 u 387 1024 377 0.977 0.469 0.916 127.127.1.1 .SFCL. 13 l - 64 0 0.000 0.000 0.000
From the FMC UI, verify the NTP server values from System > Configuration > Time Synchronization.
Enable Name Resolution and Check Reachability to tools.cisco.com
Ensure the FMC can resolve an FQDN and has reachability to tools.cisco.com:
> expert admin@FMC2000-2:~$ sudo su Password: root@FMC2000-2:/Volume/home/admin# ping tools.cisco.com PING tools.cisco.com (173.37.145.8) 56(84) bytes of data. 64 bytes from tools2.cisco.com (173.37.145.8): icmp_req=1 ttl=237 time=163 ms 64 bytes from tools2.cisco.com (173.37.145.8): icmp_req=2 ttl=237 time=163 ms
From the FMC UI, verify the management IP and DNS server IP from System > Configuration > Management Interfaces.
Verify HTTPS (TCP 443) access from FMC to tools.cisco.com
Use Telnet or curl command to ensure the FMC has HTTPS access to tools.cisco.com. If the TCP 443 communication is broken, verify it is not blocked by a firewall and there is no SSL decryption device in the path.
root@FMC2000-2:/Volume/home/admin# telnet tools.cisco.com 443 Trying 72.163.4.38... Connected to tools.cisco.com. Escape character is '^]'. ^CConnection closed by foreign host. <--- Press Ctrl+C
Curl test:
root@FMC2000-2:/Volume/home/admin# curl -vvk https://tools.cisco.com * Trying 72.163.4.38... * TCP_NODELAY set * Connected to tools.cisco.com (72.163.4.38) port 443 (#0) * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/certs/ca-certificates.crt CApath: none * TLSv1.2 (OUT), TLS header, Certificate Status (22): * TLSv1.2 (OUT), TLS handshake, Client hello (1): * TLSv1.2 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS change cipher, Change cipher spec (1): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / AES128-GCM-SHA256 * ALPN, server accepted to use http/1.1 * Server certificate: * subject: C=US; ST=CA; L=San Jose; O=Cisco Systems, Inc.; CN=tools.cisco.com * start date: Sep 17 04:00:58 2018 GMT * expire date: Sep 17 04:10:00 2020 GMT * issuer: C=US; O=HydrantID (Avalanche Cloud Corporation); CN=HydrantID SSL ICA G2 * SSL certificate verify ok. > GET / HTTP/1.1 > Host: tools.cisco.com > User-Agent: curl/7.62.0 > Accept: */* > < HTTP/1.1 200 OK < Date: Wed, 17 Jun 2020 10:28:31 GMT < Last-Modified: Thu, 20 Dec 2012 23:46:09 GMT < ETag: "39b01e46-151-4d15155dd459d" < Accept-Ranges: bytes < Content-Length: 337 < Access-Control-Allow-Credentials: true < Access-Control-Allow-Methods: GET, POST, PUT, DELETE, OPTIONS < Access-Control-Allow-Headers: Content-type, fromPartyID, inputFormat, outputFormat, Authorization, Content-Length, Accept, Origin < Content-Type: text/html < Set-Cookie: CP_GUTC=10.163.4.54.1592389711389899; path=/; expires=Mon, 16-Jun-25 10:28:31 GMT; domain=.cisco.com < Set-Cookie: CP_GUTC=10.163.44.92.1592389711391532; path=/; expires=Mon, 16-Jun-25 10:28:31 GMT; domain=.cisco.com < Cache-Control: max-age=0 < Expires: Wed, 17 Jun 2020 10:28:31 GMT < <html> <head> <script language="JavaScript"> var input = document.URL.indexOf('intellishield'); if(input != -1) { window.location="https://intellishield.cisco.com/security/alertmanager/"; } else { window.location="http://www.cisco.com"; }; </script> </head> <body> <a href="http://www.cisco.com">www.cisco.com</a> </body> </html> * Connection #0 to host tools.cisco.com left intact root@FMC2000-2:/Volume/home/admin# DNS Verification
Verify successful resolve to tools.cisco.com:
root@FMC2000-2:/Volume/home/admin# nslookup tools.cisco.com Server: 192.0.2.100 Address: 192.0.2.100#53 Non-authoritative answer: Name: tools.cisco.com Address: 72.163.4.38
Proxy Verification
If apProxy is used, check the values on both the FMC and the proxy server-side. On the FMC, check if the FMC uses the correct proxy server IP and port.
root@FMC2000-2:/Volume/home/admin# cat /etc/sf/smart_callhome.conf KEEP_SYNC_ACTIVE:1 PROXY_DST_URL:https://tools.cisco.com/its/service/oddce/services/DDCEService PROXY_SRV:192.0.xx.xx PROXY_PORT:80
In the FMC UI, the proxy values can be confirmed from System > Configuration > Management Interfaces.
If the FMC-side values are correct, check the proxy server-side values (for example, if the proxy server permits access from the FMC and to tools.cisco.com. Additionally, permit traffic and certificate exchange through the proxy. The FMC uses a certificate for the Smart License registration).
Expired Token ID
Verify the issued token ID is not expired. If it is expired, ask the Smart Software Manager administrator to issue a new token and re-register the Smart License with the new Token ID.
Change the FMC Gateway
There can be cases where Smart License authentication cannot be performed correctly due to the effects of a relay proxy or SSL decryption device. If possible, change the route for the FMC internet access to avoid these devices, and retry the Smart License registration.
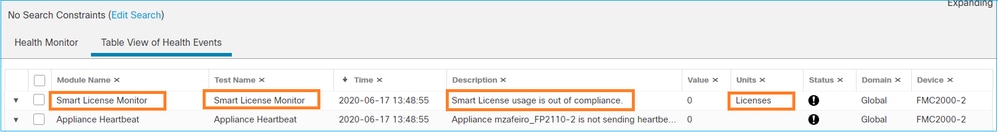
Check the Health Events on FMC
On the FMC, navigate to System > Health > Events and check the status of the Smart License Monitor module for errors. For example, if the connection fails due to an expired certificate; an error, such as id certificated expired is generated, as shown in this image.
Check the Event Log on the SSM Side
If the FMC can connect to the CSSM, check the event log of the connectivity in Inventory > Event Log. Check if there are such event logs or error logs in the CSSM. If there is no problem with the values/operation of the FMC site, and there is no event log on the CSSM side, there is a possibility it is a problem with the route between the FMC and the CSSM.
Summary of Registration and Authorization States:
| Product Registration State | Usage Authorization State | Comments |
| Unregistered | -- | The FMC is in neither Registered nor Evaluation mode. This is the initial state after FMC installation or after 90-day Evaluation License Expiration. |
| Registered | Authorized | The FMC is registered with the Cisco Smart Software Manager (CSSM) and there are FTD devices registered with a valid subscription. |
| Registered | Authorization Expired | The FMC failed to communicate with the Cisco License backend for more than 90 days. |
| Registered | Unregistered | The FMC is registered with the Cisco Smart Software Manager (CSSM), but there are no FTD devices registered on the FMC. |
| Registered | Out-of-Compliance | The FMC is registered with the Cisco Smart Software Manager (CSSM), but there are FTD devices registered with an invalid subscription(s). For example, an FTD (FP4112) device uses THREAT subscription, but with the Cisco Smart Software Manager (CSSM) there are no THREAT subscriptions available for FP4112. |
| Evaluation (90 days) | N/A | The evaluation period is in use, but there are no FTD devices registered on the FMC. |
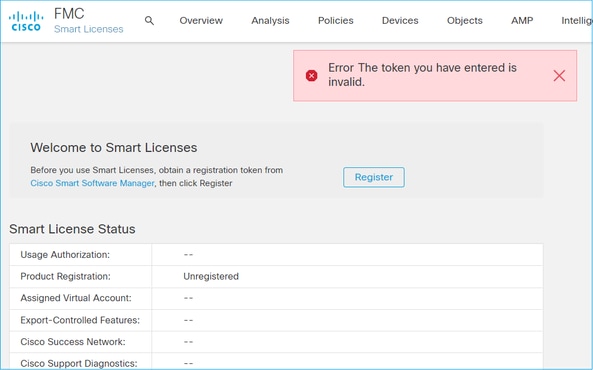
Case Study 1. Invalid Token
Symptom: Registration to the CSSM fails quickly (~10s) due to invalid token, as shown in this image.
Resolution: Use a valid token.
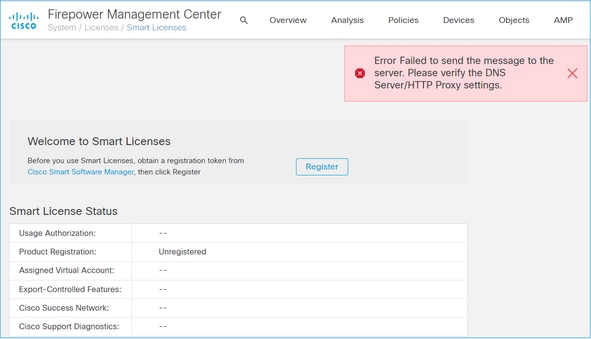
Case Study 2. Invalid DNS
Symptom: Registration to the CSSM failed after a while (~25s), as shown in this image.
Check the /var/log/process_stdout.log file. The DNS issue is seen:
root@FMC2000-2:/Volume/home/admin# cat /var/log/process_stdout.log 2020-06-25 09:05:21 sla[24043]: *Thu Jun 25 09:05:10.989 UTC: CH-LIB-ERROR: ch_pf_curl_send_msg[494],
failed to perform, err code 6, err string "Couldn't resolve host name"
Resolution: CSSM hostname resolution failure. The resolution is to configure DNS, if not configured, or fix the DNS issues.
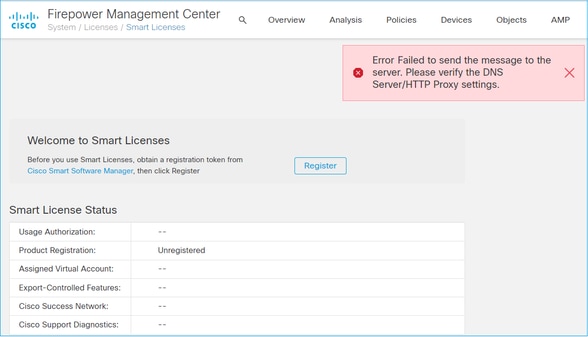
Case Study 3. Invalid Time Values
Symptom: Registration to the CSSM failed after a while (~25s), as shown in this image.
Check the /var/log/process_stdout.log file. The certificate issues are seen:
2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:39.716 UTC: CH-LIB-TRACE: ch_pf_curl_request_init[59], request "POST", url "https://tools.cisco.com/its/service/oddce/services/DDCEService" 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:39.716 UTC: CH-LIB-TRACE: ch_pf_curl_post_prepare[299], https related setting 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:39.716 UTC: CH-LIB-TRACE: ch_pf_curl_post_prepare[302], set ca info 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:39.716 UTC: CH-LIB-TRACE: ch_pf_curl_head_init[110], init msg header 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:40.205 UTC: CH-LIB-ERROR: ch_pf_curl_send_msg[494],
failed to perform, err code 60, err string "SSL peer certificate or SSH remote key was not OK" 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:40.205 UTC: CH-LIB-TRACE: ch_pf_http_unlock[330], unlock http mutex. 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:40.205 UTC: CH-LIB-TRACE: ch_pf_send_http[365], send http msg, result 30 2021-06-25 09:22:51 sla[24043]: *Fri Jun 25 09:22:40.205 UTC: CH-LIB-TRACE: ch_pf_curl_is_cert_issue[514],
cert issue checking, ret 60, url https://tools.cisco.com/its/service/oddce/services/DDCEService
Check the FMC time value:
root@FMC2000-2:/Volume/home/admin# date Fri Jun 25 09:27:22 UTC 2021
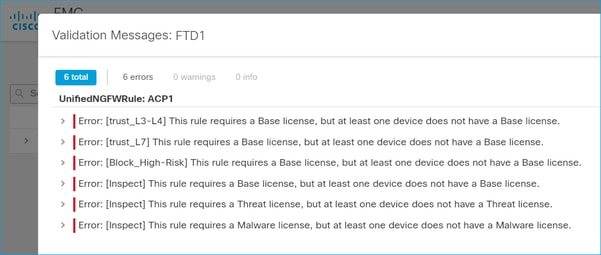
Case study 4. No Subscription
If there is no license subscription for a specific feature, the FMC deployment is not possible:
Resolution: There is a need to purchase and apply the required subscription to the device.
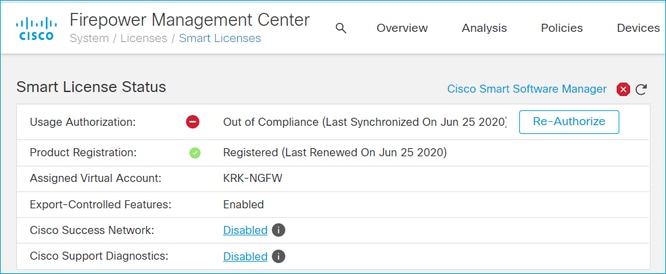
Case study 5. Out-of-Compliance (OOC)
If there is no entitlement for FTD subscriptions, the FMC Smart License goes to the out-of-compliance (OOC) state:
In the CSSM, check the Alerts for errors:
Case study 6. No Strong Encryption
If only the Base License is used, Data Encryption Standard (DES) encryption is enabled in the FTD LINA engine. In that case, deployments like L2L Virtual Private network (VPN) with stronger algorithms fail:
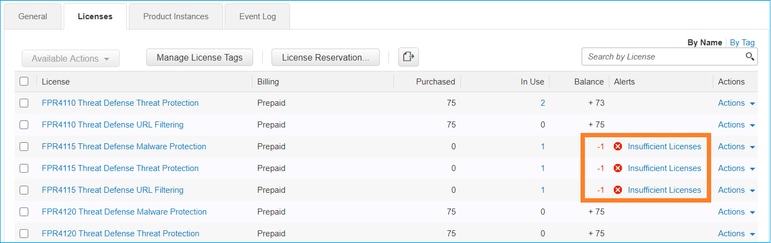
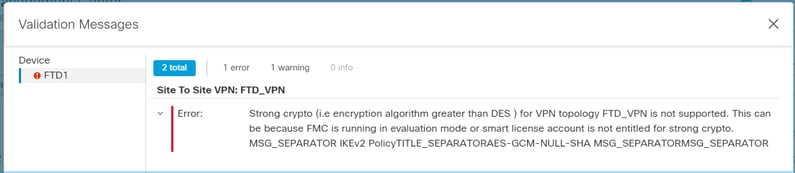
Resolution: Register the FMC to the CSSM and have a Strong Encryption attribute enabled.
Set Notification of Smart License State
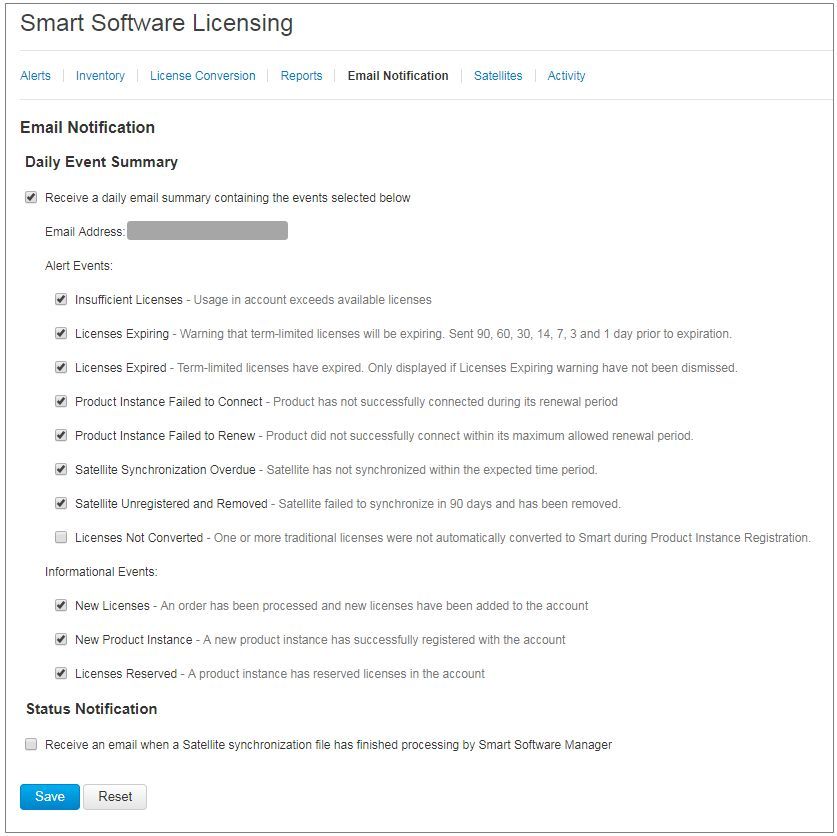
Email Notification by SSM
On the SSM side, SSM Email Notification allows reception of summary emails for various events. For example, notification for a lack of license or for licenses that are about to expire. Notifications of product instance connection or of update failure can be received.
This function is very useful to notice and prevent the occurrence of functional restrictions due to license expiration.
Get Health Alert Notifications from the FMC
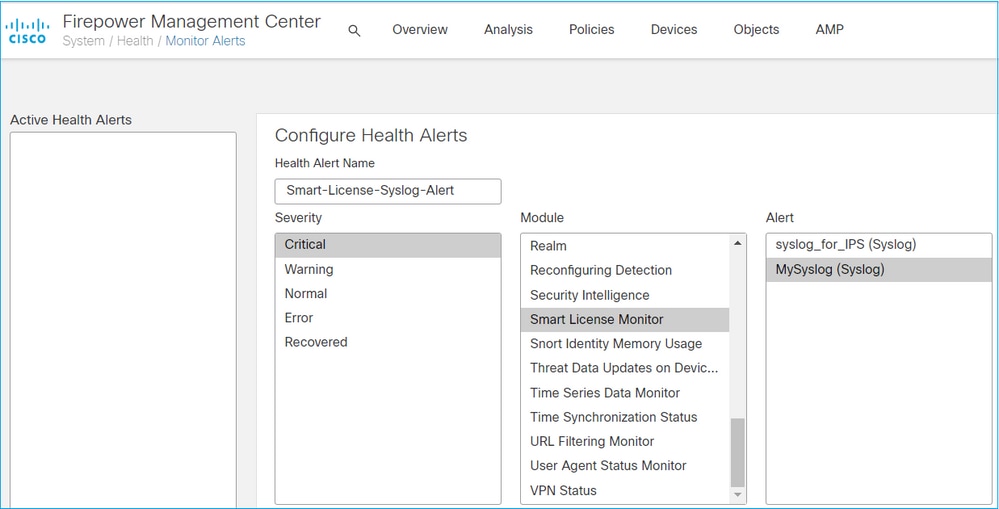
On the FMC side, it is possible to configure a Health Monitor Alert and receive an alert notification of a health event. The Module Smart License Monitor is available to check the Smart License status. The monitor alert supports Syslog, Email, and SNMP trap.
This is a configuration example to get a Syslog message when a Smart License monitor event occurs:
This is an example of a Health Alert:
The Syslog message generated by the FMC is:
Mar 13 18:47:10 xx.xx.xx.xx Mar 13 09:47:10 FMC : HMNOTIFY: Smart License Monitor (Sensor FMC): Severity: critical: Smart License usage is out of compliance
Refer to the Health Monitoring for additional details about the Health Monitor Alerts.
Multiple FMCs on the Same Smart Account
When multiple FMCs are used on the same Smart Account, each FMC hostname must be unique. When multiple FMCs in CSSM are managed, to distinguish each FMC, the hostname of the each FMC must be unique. This is useful for FMC Smart License maintenance in operation.
FMC Must Maintain Internet Connectivity
After registration, the FMC checks the Smart License Cloud and license status every 30 days. If the FMC cannot communicate for 90 days, the licensed function is maintained, but it remains in Authorization Expired status. Even in this state, the FMC tries continuously to connect to the Smart License Cloud.
Deploy Multiple FMCv
When the Firepower System is used in a virtual environment, clone (hot or cold) is not officially supported. Each Firepower Management Center virtual (FMCv) is unique because it has authentication information inside. To deploy multiple FMCv, the FMCv must be created from the Open Virtualization Format (OVF) file one at a time. For more information about this limitation, refer to the Cisco Firepower Management Center Virtual for VMware Deployment Quick Start Guide.
In FTD HA, how many device licenses are required?
When two FTDs are used in High Availability, a license is required for each device. For example, two Threat and Malware licenses are needed if the Intrusive Protection System (IPS) and Advanced Malware Protection (AMP) feature are used on the FTD HA pair.
Why are no AnyConnect licenses used by FTD?
After FMC registration to the Smart Account, ensure the AnyConnect License is enabled. To enable the license, navigate to FMC > Devices, choose your device, and select License. Select thePencil icon , choose the license that is deposited in the Smart Account, and select Save.
Why is only one AnyConnect license 'In Use' in the Smart Account when 100 users are connected?
This is expected behavior, as Smart Account tracks the number of devices that have this license enabled, not active users connected.
Why is there the error Device does not have the AnyConnect License after configuration and deployment of a Remote Access VPN by the FMC?
Ensure the FMC is registered to the Smart License Cloud. The expected behavior is Remote Access configuration cannot be deployed when the FMC is unregistered or in Evaluation mode. If the FMC is registered, ensure the AnyConnect License exists in your Smart Account and it is assigned to the device.
To assign a license, navigate to FMC Devices, select your device, License (Pencil icon) . Choose the license in the Smart Account and select Save .
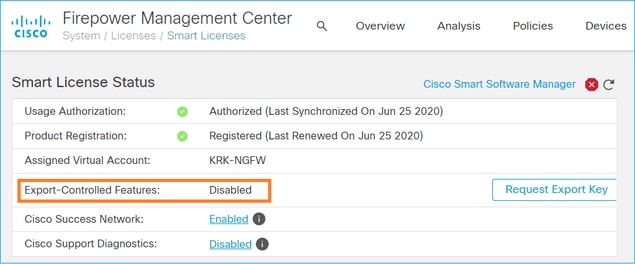
Why is there the error Remote Access VPN with SSL cannot be deployed when Export-Controlled Features (Strong-crypto) are disabled when there is a deployment of a Remote Access VPN configuration?
The Remote Access VPN deployed on the FTD requires a Strong Encryption license to be enabled. En sure a Strong Encryption license is enabled on the FMC. To check the status of the Strong Encryptionl license, navigate to the FMC System > Licenses > Smart Licensing and verify Export-Controlled Features are enabled.
How to enable a Strong Encryption License if Export-Controlled Features is disabled?
This functionality is enabled automatically if the token used during the registration of the FMC to the Smart Account Cloud has the option Allow export-controlled functionality on the products registered with this token enabled. If the token does not have this option enabled, de-register the FMC and register it again with this option enabled.
What can be done if the option 'Allow export-controlled functionality on the products registered with this token' is not available when the token is generated?
Contact your Cisco Account team.
Why is the error 'Strong crypto (that is, encryption algorithm greater than DES) for VPN topology s2s is not supported' received?
This error is displayed when the FMC uses Evaluation mode or the Smart License Account is not entitled to a Strong Encryption license. V erify the FMC is registered to the License Authority and Allow export-controlled functionality on the products registered with this token is enabled. If the Smart Account is not allowed to use a Strong Encryption license, deployment of VPN Site-to-Site configuration with ciphers stronger than DES is not allowed.
Why is an 'Out of Compliance' status on the FMC received?
The device can become out of compliance when one of the managed devices uses unavailable licenses.
How can the 'Out of Compliance' status be corrected?
Follow the steps described in the Firepower Configuration Guide:
1. Look at the Smart Licenses section at the bottom of the page to determine which licenses are needed.
2. Purchase the required licenses through your usual channels.
3. In Cisco Smart Software Manager ( https://software.cisco.com/#SmartLicensing-Inventory) , verify the licenses appear in your virtual account.
4. In the FMC, select System > Licenses > Smart Licenses.
5. Select Re-Authorize.
The full procedure can be found in Licensing the Firepower System.
What are the Firepower Threat Defense Base features?
The Base license allows:
- Configuration of FTD devices to switch and route (which includes DHCP Relay and NAT).
- Configuration of FTD devices in a high availability (HA) mode.
- Configuration of security modules as a cluster within a Firepower 9300 chassis (intra-chassis cluster).
- Configuration of Firepower 9300 or Firepower 4100 series devices (FTD) as a cluster (inter-chassis cluster).
- Configuration of user and application control and addition of user and application conditions to access control rules.
How can the Firepower Threat Defense Base Features License be obtained?
A Base license is automatically included with every purchase of a Firepower Threat Defense or Firepower Threat Defense Virtual device. It is automatically added to your Smart Account when FTD registers to the FMC.
Which IP addresses must be allowed in the path between the FMC and the Smart License Cloud?
The FMC uses the IP address on port 443 to communicate with the Smart License Cloud.
That IP address ( https://tools.cisco.com) is resolved to these IP addresses:
- 72.163.4.38
- 173.37.145.8
-
Firepower Management Center Configuration Guides
-
Cisco Live Smart Licensing Overview: BRKARC-2034
-
Cisco Secure Firewall Management Center Feature Licenses
-
Cisco Smart Software Licensing Frequently Asked Questions (FAQs)
burkhartlinquis1995.blogspot.com
Source: https://www.cisco.com/c/en/us/support/docs/security/firepower-management-center/215838-fmc-and-ftd-smart-license-registration-a.html
0 Response to "Failed to Connect to Firepower Continuing Without It"
Post a Comment